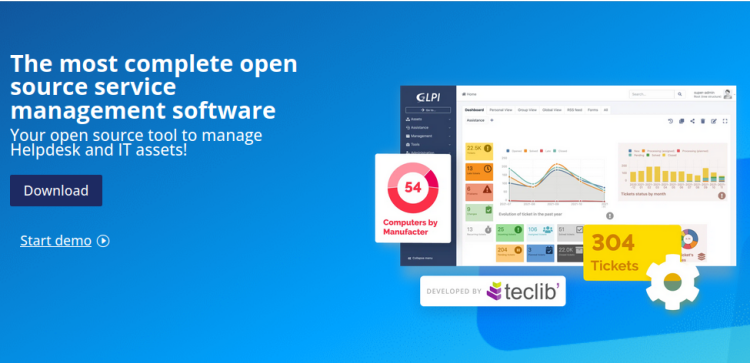
GLPI stands for Gestionnaire Libre de Parc Informatique is a Free Asset and IT Management Software package, that provides ITIL Service Desk features, licenses tracking and software auditing.
Read MoreTag: research

Advisory | Seagate Central Storage Remote Code Execution 0day
In this article, I will be sharing several critical vulnerabilities of Seagate Central Storage NAS product.
Read More